top of page
Search

Explaination of BIOS on laptops.
BIOS (basic input/output system) is the program a computer's microprocessor uses to start the computer system after it is powered on. It...

theblackthreat
Nov 8, 20214 min read

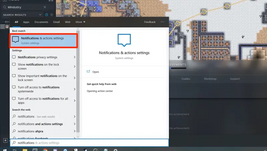
How to turn off notifications on Windows 10
If you've been using Windows 10 for long enough, you're probably used to being swarmed by notifications. It seems like every program has...

theblackthreat
Nov 8, 20211 min read


How to Upgrade Window 7 to Window 8.1
Before You Begin While Windows 8.1 will retain some of your information after you upgrade, we wouldn't recommend you count on that. Make...

theblackthreat
Nov 8, 20212 min read

How to Connect Android to Windows
Step 1: Open Your Phone in windows PC. Then click on Get started. Step 2 : Sign In Step 3 : Download app on android phone. Step 4 : Scan...

theblackthreat
Nov 8, 20211 min read


How to Dual Boot with windows & Linux
If you are not a fan of Windows 10, then don’t worry — with this tutorial you can also dual boot Kali Linux with Windows 7/8/8.1....

theblackthreat
Nov 8, 20214 min read


How to recover Data in Android.
Accidentally deleting the files on your phone can be very frustrating. However, your files are never lost forever. If you have an Android...

theblackthreat
Nov 8, 20212 min read


How to Recover Data in Windows.
Did you accidentally delete an important file? Did you also empty the Recycle Bin? Don't worry. Microsoft added a new file recovery tool...

theblackthreat
Nov 8, 20214 min read

Windows Command Prompt tutorial
Here's a simple tutorial to the command line for beginners if you're not familiar with Windows' Command Prompt. A lot of Windows users...

theblackthreat
Nov 8, 20215 min read


How to add Nodejs environment in windows.
In this post, we will discuss about “How to setup Node JS Base Environment” in Windows OS 1. Access Node JS Official Website...

theblackthreat
Nov 8, 20212 min read

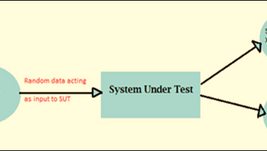
Fuzzing Hacking technique
Fuzzing is the usually automated process of entering random data into a program and analyzing the results to find potentially exploitable bu

theblackthreat
Nov 8, 20214 min read


15 Powerful Gadgets For Ethical Hackers
In order to complete their tasks, penetration testers require not only software but also hardware. We'll go over the hardware devices and...

theblackthreat
Nov 8, 20216 min read

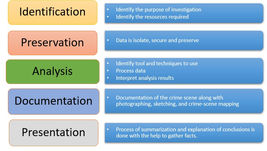
Basics of Digital Forensics
What is Digital Forensics? Digital Forensics is defined as the process of preservation, identification, extraction, and documentation of...

theblackthreat
Oct 26, 20213 min read
Everything about Cross-Site Scripting (XSS)
Cross-site Scripting (XSS) Cross-site Scripting (XSS) is a client-side code injection attack. The attacker aims to execute malicious...

theblackthreat
Oct 26, 20218 min read


How to Install Telegram and Signal on Linux
In this detailed article we are going to discuss how we can install Signal and Telegram on our Linux System, we are using Kali Linux here. B

theblackthreat
Oct 26, 20213 min read


How to Own All Git Repositories and SVN Repositories
Yes, this vulnerability exists because most of the time when using a version-controlled system, developers host their repository in producti

theblackthreat
Oct 26, 20212 min read

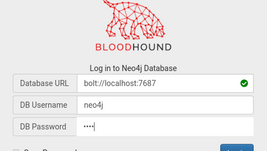
How to Install and Configure BloodHound on Kali Linux
What is BloodHound? BloodHound is a single-page Javascript web application, built on top of Linkurious, compiled with Electron, with a...

theblackthreat
Oct 26, 20211 min read
©2022 www.theblackthreat.in All right reserved.
bottom of page



